In a comprehensive annual report released by web3 security firm Scam Sniffer, alarming statistics highlight the growing threat of phishing scams in the crypto industry. According to the report, these scams resulted in the theft of approximately $300 million of cryptocurrencies.
Rising Tide Of Sophisticated Crypto Scams
Per the report, phishing activities have surged throughout the year, with scammers employing increasingly “sophisticated tactics” to evade security measures. Notably, Scam Sniffer identified a type of malware called “Wallet Drainers,” which has gained significant traction and posed a severe risk during the past year.
These malicious software are deployed on phishing websites, deceiving users into signing malicious transactions and subsequently siphoning assets from their cryptocurrency wallets.
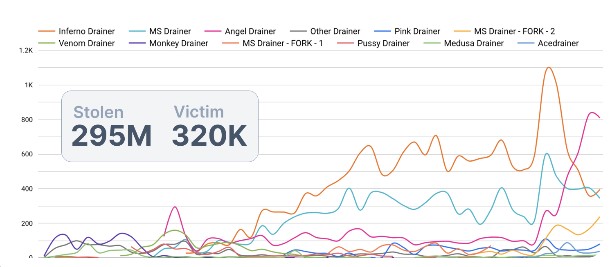
The report notes that the impact of these phishing activities has been devastating, affecting ordinary users in various forms and resulting in substantial financial losses. Scam Sniffer’s monitoring revealed that Wallet Drainers stole nearly $295 million in assets from approximately 324,000 victims in 2023.
One particularly alarming incident occurred on March 11, with almost $7 million stolen in a single day. Victims encountered phishing websites impersonating Circle, and the theft was primarily attributed to fluctuations in USDC rates.
Scam Sniffer’s findings also revealed notable thefts around March 24, coinciding with the hacking of Arbitrum’s Discord. Interestingly, the report highlights that each peak in theft was associated with group-related events, such as airdrops or hacking incidents.
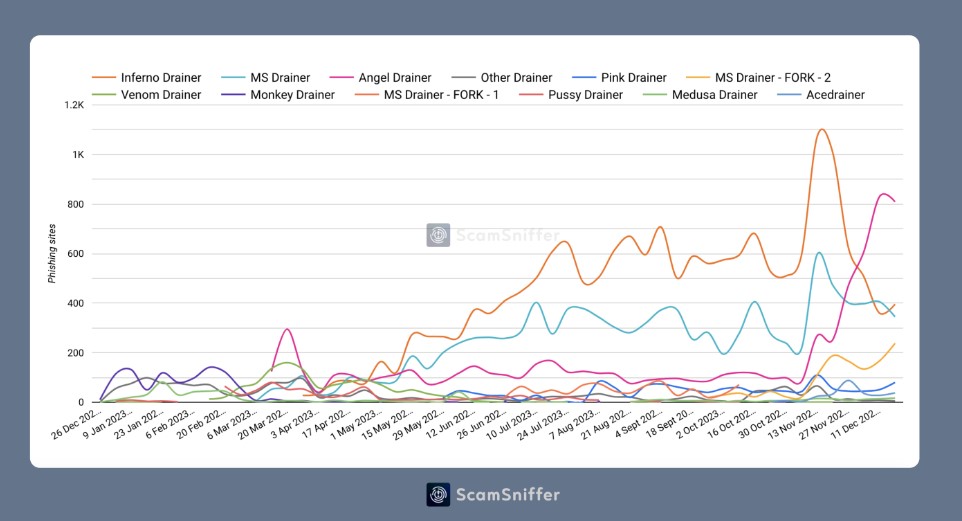
The report also identifies prominent Wallet Drainers, including Inferno Drainer, MS Drainer, Angel Drainer, Monkey Drainer, Venom Drainer, Pink Drainer, and Pussy Drainer, each responsible for significant financial losses and victim counts.
Discord, Airdrops, And Paid Traffic To Steal Crypto
The report further emphasized the “ever-evolving nature” of these phishing operations. After ZachXBT exposed Monkey Drainer, their departure was announced following six months of activity.
Venom Drainer subsequently took over a significant portion of their “clientele.” Following Venom’s cessation of services in April, other phishing gangs sought alternative providers.
Furthermore, the scale and speed of these attacks have escalated significantly. For example, Monkey Drainer drained $16 million over six months, while Inferno Drainer surpassed this figure substantially, looting a staggering $81 million in just nine months. With a 20% Drainer fee, these malicious actors profited at least $47 million from selling wallet drainer services.
Phishing sites acquire traffic through various methods, including hacking official project Discord and X (formerly Twitter) accounts, attacks on official project frontends or libraries used, and airdrops of non-fungible tokens (NFTs).
While the community often responds quickly to hacking attacks, other methods, such as airdrops and organic or paid traffic, can go largely unnoticed, the report notes.
Scam Sniffer’s continuous efforts in combating these threats involve scanning nearly 12 million URLs and identifying almost 145,000 malicious URLs.
The company’s open-source blacklist currently contains close to 100,000 malicious domains, and they actively collaborate with platforms like Chainabuse to expose and mitigate these malicious websites.
Ultimately, Scam Sniffer aims to enhance the public’s understanding of phishing threats and contribute to a more secure web3 ecosystem by raising awareness and sharing information about significant theft cases on social media platforms.
Featured image from Shutterstock, chart from TradingView.com