In the ever-evolving landscape of cybercrime, a new threat has emerged, leaving individuals and businesses vulnerable to financial losses and privacy breaches – Inferno Drainer. The Inferno Drainer phishing scam, aptly named for its ability to drain victims’ resources, has recently come to the forefront of crypto evolution.
This sophisticated “scam-as-a-service” operation has already pilfered an astonishing $5.9 million since March, underscoring the urgent need for increased vigilance and robust security measures.
Inferno Drainer’s sophisticated phishing scam leaves millions vulnerable
Operating behind a veil of anonymity, the Inferno Drainer has quickly gained notoriety within the dark web. The group behind this scam-as-a-service operation remains shrouded in mystery, employing advanced techniques to evade detection by law enforcement agencies and cybersecurity experts.
According to the Web3 scam-detection firm Scam Sniffer, a new fraud as a service called “Inferno Drainer” has allegedly stolen nearly $6 million from unwitting crypto users. Inferno Drainer reportedly advertises that it provides scammers with ready-to-use code that enables them to steal crypto in exchange for a 20% share of the scammers’ cryptocurrency “loot.”
According to industry sources, the Inferno Drainer’s modus operandi revolves around sophisticated phishing tactics. The scam involves creating convincing replicas of well-known websites, such as banking portals and crypto exchanges. Unsuspecting victims are then lured into divulging their sensitive login credentials and personal information, which is subsequently exploited by the criminals.

How does it work
The scam service was discovered by security enthusiast and alias Twitter user 0xSaiyanGod, who stumbled upon a promoter of it while perusing the Scam Sniffer Telegram channel. The security service launched an investigation after Saiyan reported the fraudster to the channel.
Scam Sniffer discovered a screenshot of a $103,000 drain transaction using a Permit2 exploit. Permit2 exploits are phishing scams that use a streamlined variation of the token approval process.
As reported by Scam Sniffer, the screenshot displayed the transaction hash of the larceny, prompting the team to search for the transaction, which led them to the address of the exploiter. Scam Sniffer then discovered that the aforementioned address was linked to over 689 phishing websites created since March 27 and had stolen $5.9 million from victims on various networks, including Ethereum, Arbitrum, Polygon, and BNB Chain.
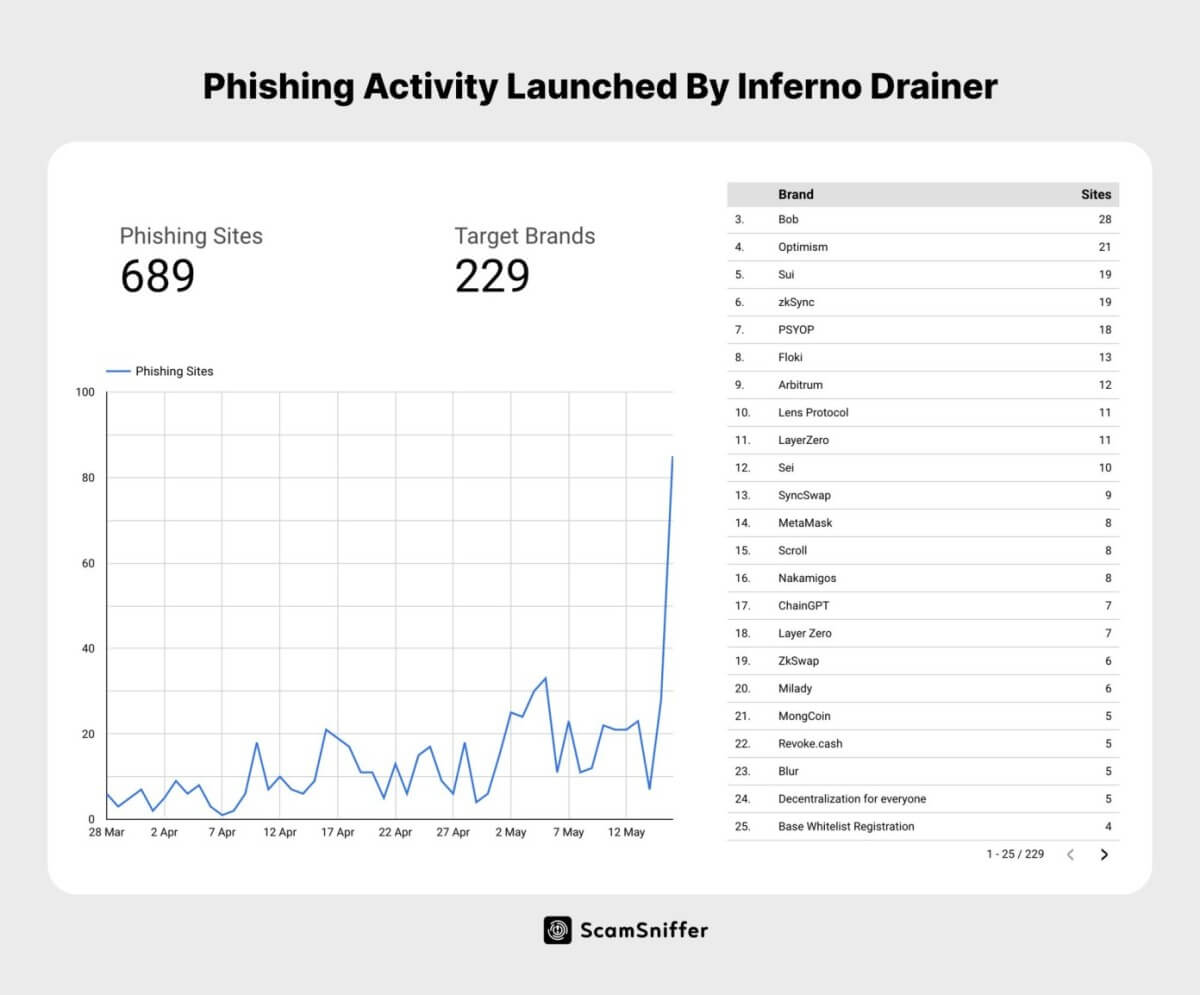
Scam Sniffer developed a Dune analytics dashboard to display the supporting data for this conclusion.
According to the report, Inferno Drainer advertised its “service” to hackers in exchange for 20% of their profits. It even offered to create phishing sites for customers in exchange for a 30% commission, but only for “good customers or people with big potential.”
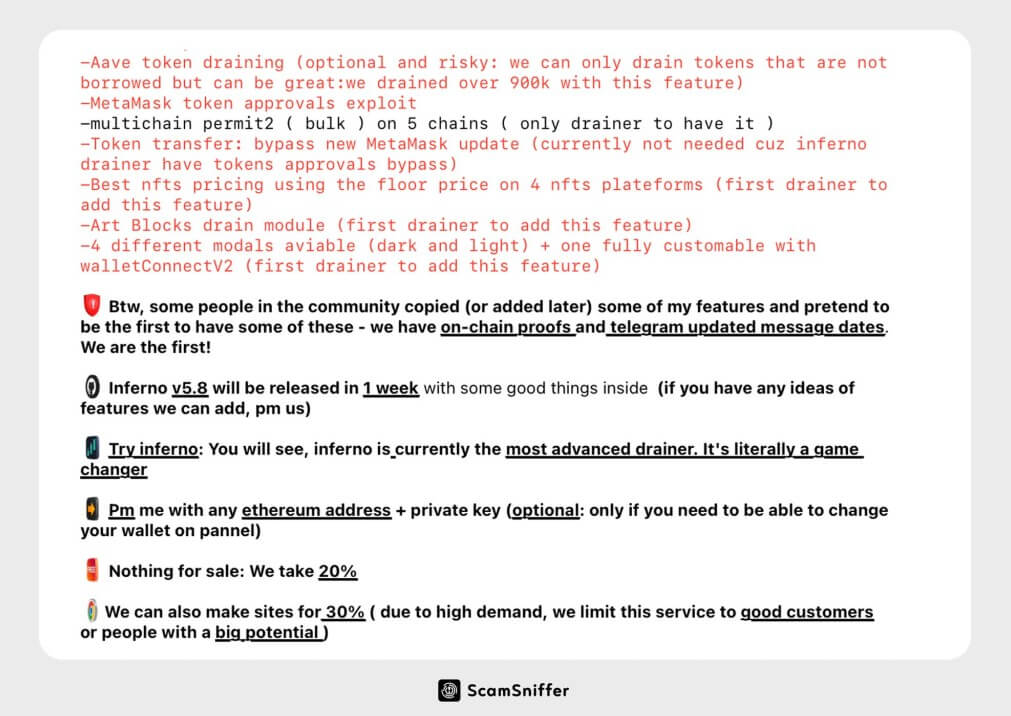
Source: Scam Sniffer – This is the alleged Telegram advertisement for Inferno Drainer.
So far, $5.9 million has been taken by analyzing data from different chains, with about 4,888 victims. The Mainnet is worth $4.3 million, Arbitrum is for $0.79 million, Polygon is worth $0.41 million, and BNB is at $0.39 million.
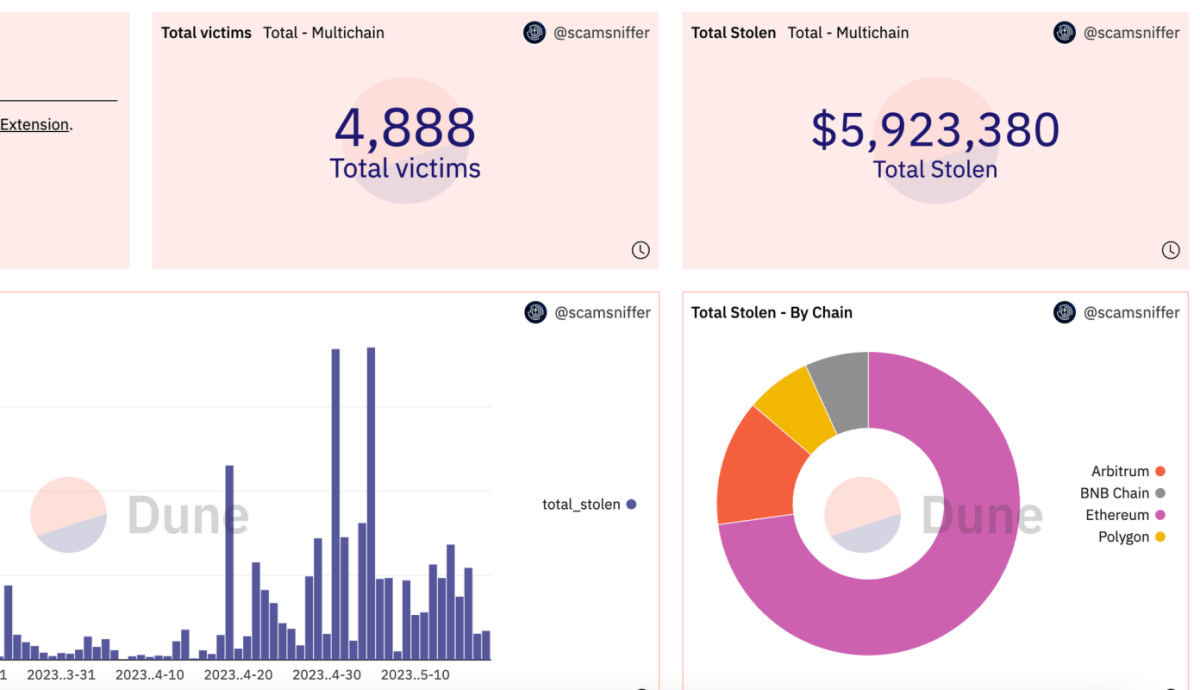
Based on an examination of the on-chain funds collection addresses, it is estimated that about 1,699 ETH was stolen and distributed among these five major addresses. They purposefully keep the cash in each address at roughly 300-400 ETH.
In the past few months, scams posing as services have become an increasing problem in the crypto community. ZachXBT discovered a comparable service named “Monkey Drainer” in October. Before shutting down in March, it stole at least $1 million in ETH from consumers.
Scam Sniffer previously uncovered a similar sort of “Scam as a Service” known as Venom Drainer. It took $27 million from 15 thousand people, with the top five victims losing $14 million in total. 530 phishing sites targeting approximately 170 brands were built.





