German authorities used a timing attack to reveal a darknet admin’s identity, but Tor claims that the suspected attack vector is outdated.
New theories have emerged about how German authorities cracked the anonymity of a darknet criminal website admin in 2021, exposing a major vulnerability in Tor’s privacy network.
While authorities haven’t released their secrets on how this was conducted, a September 2024 report speculates that they used timing analysis and compromised servers to successfully trace the IP of “Andres G,” the alleged operator of “Boystown,” a darknet site for child pornography.
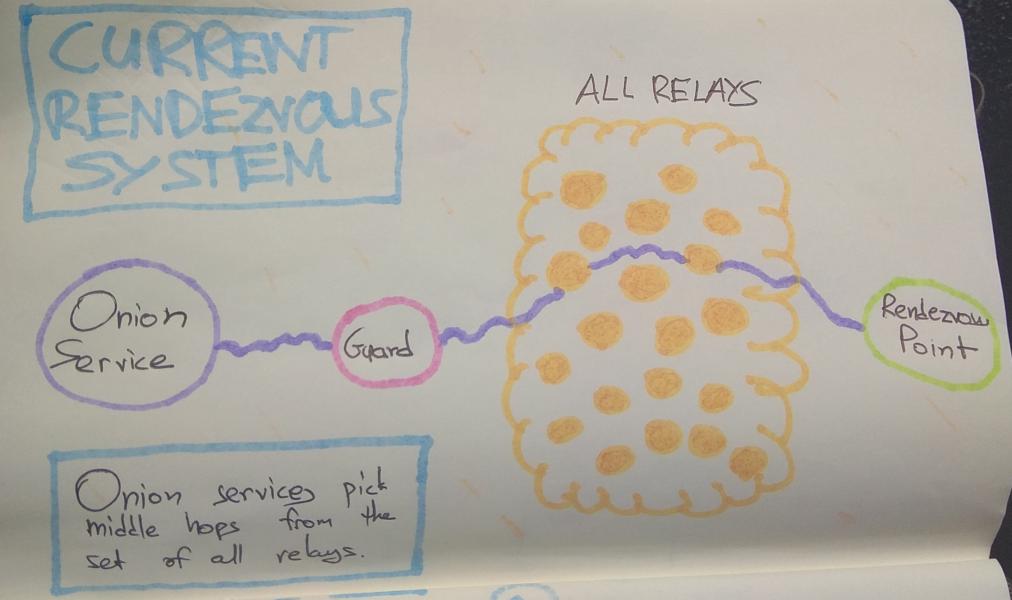
Tor itself admits that it is unaware of the exact method but suspects the German authorities’ operation leveraged an outdated chat messenger called Ricochet that the arrested criminal was using.