Microsoft points the finger at the European Union for its recent tech disaster, arguing it can’t lock down its operating system like Apple due to a 2009 deal with the European Commission.
Per WSJ, this agreement forces Microsoft to give other security software makers the same level of access to Windows that it has. The blue screen of death reappeared on millions of computers on Friday.
Security experts are saying Microsoft hasn’t taken its software’s weaknesses seriously enough. A blog post from the company stated that 8.5 million Windows machines were affected, which is less than 1% of their global presence.

But that was enough to cripple major businesses in healthcare, media, and restaurants. The chaos continued into Saturday, with nearly 2,000 flights canceled by U.S. airlines, compared to 3,400 the day before. Delta was hit hardest, canceling more than half the flights on Saturday.
This whole mess started with a faulty update sent to corporate clients by CrowdStrike, one of many cybersecurity companies trying to secure Windows. Microsoft has its own rival product, Windows Defender.

CrowdStrike’s CEO owned up to the problem on Friday and said they were working to get their customers back on track. Though his apology was found offensive, and many influential people—including Elon Musk and Stephen King—slammed him for it.
Security has always been a weak spot for Microsoft. Its software has been repeatedly targeted by criminal hackers and state-sponsored groups from Russia and China. Top executives have had to testify before Congress to explain why Windows is so vulnerable.
With decentralization, this never would have happened. By distributing data and security controls across multiple nodes, decentralized systems eliminate single points of failure.
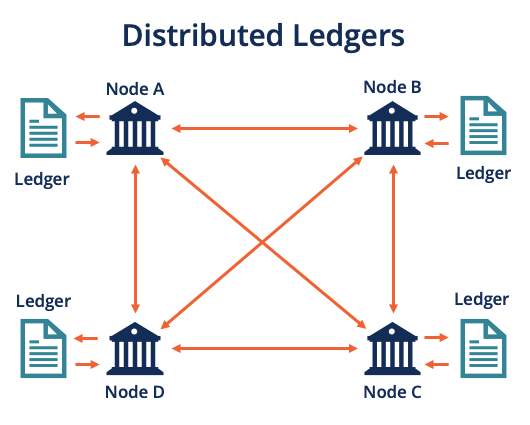
Even if one node is compromised, the overall system remains operational. So there will never be a widespread disruption like this one. Cryptographically secured and verified data makes it hard for attackers to alter or corrupt information without detection.
Decentralized agents can monitor and respond to threats independently, ensuring continuous security without a central server.





